Comprehensive Guide on Macro Virus Infections & Effective Eradication Techniques

Comprehensive Guide on Macro Virus Infections & Effective Eradication Techniques
In this digital era, it is pretty easy to get infected with a virus or malware if you are not careful. Some malware like Ransomware , Spyware are too dangerous and can create havoc in your life. However, there are a few ones that are not that dangerous but can sneakily enter your system, cause trouble in your device, and disturb your workflow. One such type of malware is Macro Virus.

Stay malware-free with reliable antivirus
Don’t compromise your Data and Privacy. TotalAV is a top-notch antivirus program that handles various viruses, trojans, and other malware that may target your devices. It will safeguard your devices and enhance your system performance.
4.9/5
⭐ Editor’s Choice
✔️ Excellent Malware Detection
✔️ Multiple set of Features
✔️ 30 Day Money-Back
If you’re reading this, then chances are that your computer is already infected with one or many macro viruses. In this guide, we will know all about Macro viruses and learn how to remove and avoid them.
How to Remove Malware and Cleanup Windows PC
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
What are Macro Viruses?
Macro viruses are a type of malware that uses macros to infect your computer. A macro is a small program that allows you to automate certain tasks in a software application. For example, you can create a macro to automatically format text in Microsoft Word and Excel.
Macros can be very helpful when used correctly but they can also be dangerous if used to create malware. Macro viruses use macros to infect your computer by hiding themselves in legitimate files like Word documents or Excel spreadsheets. When you open the infected file, the virus will run and infect your computer. They then go about replicating themselves by changing the macro commands in Microsoft Office documents to make them do malicious things like sending out spam emails to contacts on your behalf.
How does a Macro Virus spread?
Macro viruses are usually spread through email attachments, malware downloads, and social engineering. Let us discuss how exactly.
Through Email Attachment:
An infected file attached to an email is the most common way for macro viruses to spread. Macro virus-infected files look like regular documents but they contain harmful macros that can damage your system or use it as a platform for spreading the virus further. For example, cybercriminals sometimes send out emails with malicious PDF or Word attachment that looks harmless on the outside but contain a dangerous payload of macro commands inside them. These types of threats often trick users into opening these types of files because they appear legitimate due to their attractive names and logos. Once you open such a file in Microsoft Word software, it automatically starts running its macros, which can lead to your computer getting infected.
Through Malware download:
Macro viruses are also spread by malware downloads, i.e., you downloading and installing malicious software on your system without realizing it. Malicious websites use social engineering techniques like fake popup windows to trick users into visiting them or clicking links that take them there automatically. Once you visit one of these sites, the site will download an executable file onto your PC without informing you about its harmful nature because once installed, this type of software often hides from the user’s view in order to continue running undetected for as long as possible so they can cause more damage before being detected and removed from a device. In some cases, such programs might not only contain macro viruses but also other types of viruses and malware, making them even more dangerous.
Through Social engineering
Macro viruses can also spread through social engineering techniques. Social engineering is a type of hacking where cybercriminals use various methods to trick users into revealing their sensitive information like passwords or credit card details. For example, phishing emails are email messages that attempt to lure the user into clicking on a link or opening an attachment that contains the virus. These emails usually look very legitimate and often have convincing subject lines and sender addresses that make them appear as if they’re from a trusted source. As part of the scam, these emails might also ask you to provide personal information like your name, address, date of birth, etc., which can then be used to hijack your accounts and steal your identity.
How does a Macro Virus Work?
After infiltrating your system, here are the steps how a macro virus functions on your system:
- The virus first scans your computer for Microsoft Office files (Word, Excel, PowerPoint, etc.) and then uses its macros to replicate itself into other documents on the system.
- The virus also modifies the macro security level to stop Macros from being disabled, which allows it to run undetected. This is done so that if any of the macros are found by users they will be unable to disable them without emailing an administrator or contacting tech support.
- Once this step is complete, the macro virus begins using its macros to send out spam emails containing infected documents attached as attachments which contain malicious payloads like ransomware or trojans, etc. These infected documents usually appear harmless until opened in any version of Microsoft Office.
- When the user opens an infected document, macros automatically start running and infect their machine with malware.
Symptoms of Macro Virus Attack
If your system gets infiltrated with Macro viruses, it might show one or more of the following symptoms:
- You may get email messages that contain content related to your search appearing in your inbox.
- You might also notice Word or Excel files opening without your consent, i.e., when you press the “open” button, a file opens that you didn’t actually click on. This is because macros have been programmed to automatically open these files with hidden buttons or keyboard shortcuts.
- There might be some instant pop-ups appearing on your screen when you’re browsing, telling you that some of your data has become corrupted and needs fixing immediately by clicking on the “repair” button located alongside this notification (which may lead to downloading malware instead). These errors are also fake and designed to make you install malicious software.
- Malware can also be distributed through spam email campaigns using macro viruses that download malware when they are opened or executed on your computer.
- Macros can also be used to download and install malware directly onto your computer without you ever knowing. Your device might be infected with ransomware, trojans, advanced spyware, etc., which can steal personal information like login details for various accounts, credit card details, images of your passport/driver’s license/national ID card stored in the hard disk of the infected computer. So, if you observe any such thing happening on your computer, it could be the work of a Macro Virus.
- You’ll get an error message saying that macros have been disabled by default and you need to enable them. This is another social engineering technique used to trick less-technical users into enabling macros, which will give criminals full access to your system.
How to remove Macro Viruses?
To remove Macro viruses from your PC, follow these steps:
Step 1: Switch over the PC to Safe mode
Safe mode is a special way to predict the system-critical problem, which interrupts the normal operation of Windows. So, safe mode is an alternate boot method that makes it easier to diagnose adware and malware infection. There are minimum programs and services in Safe Mode
So, if any adware started to load automatically into your PC, it will remove the files which are not running or active. Let’s see the steps to switch over your PC to Safe Mode .
- For this, Login into your Windows PC and click the “start” button and tap the “Power” Hold on the Shift key, and select “Reboot”.
- From the full-screen menu, select the “troubleshooting” and then the “Advanced Options”, then opt for “Startup Settings”. So, once getting into the Startup Settings screen, tap the “restart” button from the list of settings options.
- Next, you’ll see the window with numbered options, which is hinted as “press a number to choose from the options below”. You can select number “4” (Enable Safe mode) to enter into the Safe Mode.
Step 2: Delete Temporary Files
The temporary files folder can also be a carrier of malicious files of Macro Viruses. You should delete all the temporary files and folders regularly for the smooth running of the system. Removing the temporary files would also clear the unnecessary clutter from your system and free up valuable space.
Here are the steps to remove the temporary files from the Windows 10 and Windows 11 devices.
Windows 10Windows 11
Remove Temporary Files from Windows 10
Here are the steps to eliminate the temporary files on Windows 10:
Open the Run command window.
Type %temp% and hit the enter key.

This run command would navigate you to this path: C:\Users\[username]\AppData\Local\Temp, that is, the temp folder.
Select all Files and Folders of this folder and delete them. Don’t hesitate to delete them, as they are not essential for any of your tasks.

Next right-click on the Recycle Bin and select Empty Recycle Bin.

Remove Temporary Files from Windows 11
On Windows 11, it is easy to remove Temporary files. Here are the steps:
Open Windows 11 Settings from the Start Menu.
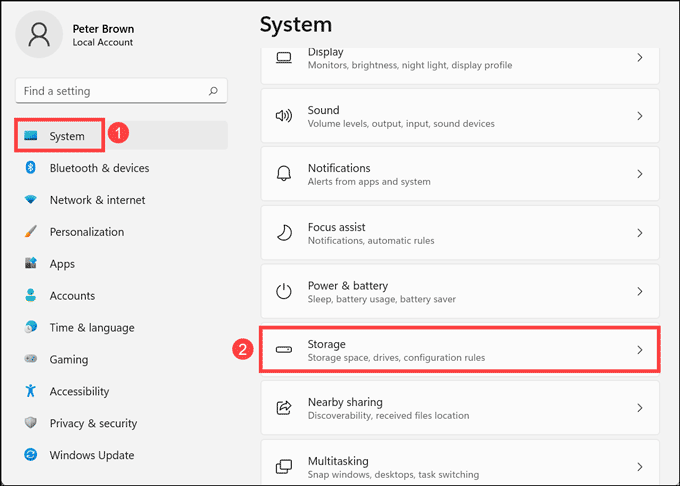
From the left pane, choose System settings and click on Storage from the right.

Click on the Temporary files option.

Tick all the boxes that you want to delete and click on Remove files.

Step 3: Uninstall Suspicious Applications
The TrickBot malware can be hidden in any application which is pretending to be useful. To remove it, uninstall all the suspicious applications you can find on the device.
Here are the steps to uninstall applications from Windows 10 and Windows 11.
Windows 10Windows 11
Uninstall Suspicious Apps on Windows 10
Right-click on the taskbar and select the Task Manager.

Watch out for the applications that are consuming the system memory even though you did not install or launch them.
Right-click on the suspicious application and open its file location.

Delete the file from its root location.
Open Control Panel and click on Uninstall a program and check for suspicious apps. One by one, select and uninstall them.

Uninstall Suspicious Apps on Windows 11
Right-click on the Start button and select Task Manager from the list.

Look out for the applications which are unnecessarily consuming the system resources without actively running.
Right-click on such applications and open their file location.

Delete all files from the targeted folder. Some files won’t be deleted as the application is still active.
Open Control Panel and click on Uninstall a program.

Check for suspicious apps. One by one, select and uninstall them.

Step 4: Remove System Restore Points
The system restore points can also have the potential to contain the malicious files of the Macro virus. So, it is important to delete those to ensure that all the traces of the virus are removed from your PC.
- To do this, press the “Windows + pause break” keys to open the System window from the control panel and choose the “System protection”.

- From the System Properties window, select the drive whose system protection is located (Local Disk: C) and click “Configure” and “Ok”.

3. Tap the “Delete” button to delete the restore points for your system. Now, the small confirmation dialog window will persist, click “continue” to remove all the restore points on the selected drive.
Step 5: Reset Web Browser Settings
Browsers are the Gateway for Malware like Trojan, Adware, browser hijackers, and others. The Macro virus can enter your system in many ways, but mostly browsers are the gateway for them. There is definitely a risk involved when you download a file from unofficial websites or an attachment from an unsolicited email. Along with that, security vulnerabilities in the web browser programs themselves might sometimes lead to malware exploit.
It is best to reset the browser to its original state after the trojan infection. Here are the ways to reset different web browsers.
Google ChromeMozilla FirefoxMicrosoft Edge
Reset Google Chrome Browser
Here are the steps to reset the Google Chrome browser:
Launch Google Chrome, click on three dots at the top right corner, and choose Settings from the menu.

On the Settings page, click on the Advanced at the left pane.

Under Advanced settings, click on Reset and clean up.

Next, click on the Reset Settings button to finish resetting the Chrome Browser.

How to Control a Chrome Extension’s Permissions
Reset Mozilla Firefox Browser
Follow these steps to reset the Mozilla Firefox:
Open Mozilla Firefox, click on the menu button at the top right corner, and select Help.

Under Firefox Help, choose More troubleshooting information.

On the Troubleshooting Information page, click on the Refresh Firefox button under Give Firefox a tune up. This is on the right side of the page.

On the warning pop-up, click on Refresh Firefox.

Reset Microsoft Edge Browser
On Microsoft Edge, follow these instructions to reset it:
Launch Edge browser, click on three horizontal dots at top right corner, and select Settings from the menu.

Under the settings page, click on Reset settings on the left pane.

Click on Restore settings to their default value.

Next, on the Restore settings pop-up, click on the Reset button.

Step 6: Install an Antimalware and Perform a Scan
Manually removing malware can be a tedious task, and it takes a lot of time and effort on our part. Sometimes, it may get irritated for you if you are not much into the technology. There is no need to worry; you can get a robust antimalware like MalwareFox that will scan for malware and remove it.
Though TrickBot tends to hide from the security programs or disable them, that’s not the case with MalwareFox. It is reliable security software that promises to protect your system and helps to handle malware and viruses. MalwareFox will scan, detect, and remove Malware and offers real-time protection. It also protects your PC from the most dangerous malware such as Ransomware, Zero-Day Attack protection, Grayware, Keyloggers, etc.
- Download Malwarefox Trojan Remover and install it.
- Perform a full system scan to get rid of every malware that is troubling your system.

How to prevent Macro Virus attacks?
The best way to avoid a macro virus attack is to follow proper security best practices.
- First and foremost, always keep your system and installed antivirus application up-to-date. Most anti-virus vendors provide regular updates for new threats on a daily basis, so make sure you install all of these patches to get maximum protection from viruses and malware.
- Disable macros in Microsoft Word and other MS apps when not required, as they pose a major security risk. When macros are disabled (which is the default setting), no code will run automatically without your consent or knowledge. This can be done by going into the “Preferences” of each application, which will tell you what settings need to be enabled or disabled for this feature to work properly.
- Macro viruses can be prevented easily by having an advanced spam filter feature on your email client and keeping it up-to-date at all times.
- Never open email attachments from unknown senders, even when they come with proper file extensions like .PDF, .DOCX, etc., which may be attached.
Conclusion
Though Macro viruses are almost extinct because of the rise in popularity of JavaScript virus attacks, they are still dangerous. They might not immediately do any damage in the sense that they don’t steal your credit card numbers or transfer money from your account without your consent, but they can still do a lot of other things like stealing sensitive data, blocking important files on the computer system, distorting data in certain applications, etc.
Computer users need to be cautious when it comes to opening email attachments from unknown senders, browsing through spam emails, or downloading anything from untrusted sources. Be extra careful if you’re a company employee and your job involves sending out confidential information to clients/colleagues. The guide will help you to know everything about Macro Virus and how to tackle it.
How to enable macros in Microsoft applications?
Macros are disabled by default on all versions of Office suite for security reasons, so you’ll need to enable them manually to run the program successfully. This can be done by going into “Preferences” and finding the option that allows or disables macros for each application. You will have to select the “Trust Center” tab first before clicking on “enable this content”.
How to deal with Macro Virus?
The best way to prevent Macro Virus attacks is to follow the security best practices mentioned above and ensure that you’ve installed all recent updates from your anti-virus vendor. This includes enabling macros only when required (which should be rare), updating your spam filter feature frequently, and not opening any email attachments from unknown senders.
What other kinds of viruses are similar to macro viruses?
There are many kinds of viruses like boot sector virus, stealth virus, polymorphic virus, and memory-resident virus which infects disk sectors and allows other malicious programs/viruses to attach themselves to legitimate programs so as to conceal their presence in the computer system.
Leave a Comment Cancel reply
Comment
Name Email
Save my name, email, and website in this browser for the next time I comment.
Δ
Also read:
- [New] Adding Pizzazz to Your Footage with Moving Text
- [Updated] Step-by-Step to Smiles and Laughter Your Snapchat Gif Tutorial
- 2024 Approved IOS and PS2 Gaming Top Emulators Unveiled
- Accelerate PC Operations with Expertly Reviewed Paid & Free Software Solutions – Tips From Tech Guru at YL Software
- Best Free Mobile Apps: Transform Your Images Into Artwork with Just a Tap!
- Easy Steps for Personalizing Computer Sounds Using Windows Control Panel - Tutorial From YL Systems
- Effective Solutions: A Guide to Diagnosing and Fixing Graphics Card Issues - Tips From YL Computing's Expertise
- Exploring Causes of Fluctuating Internet Connectivity with YL Software Solutions
- Foundations of Easing Volume Control in Audition for 2024
- High-Quality BMW M3 (2019) HD Resolution Wallpaper Graphics & Desktop Backgrounds - Premium Digital Artwork by YL Computing
- In 2024, How to Mirror PC Screen to Google Pixel Fold Phones? | Dr.fone
- New 2024 Approved Mastering Audio Cut and Mix A Comprehensive Guide to Using Avidemux
- Resolved: Top Fixes for Eliminating Heart of Iron IV Game Crashes and Glitches
- Solving Your Graphic Card Issues: A Step-by-Step Guide - By YL Computing
- Step-by-Step Guide: Updating Your NVIDIA/AMD Graphics Drivers on Windows 10 - Tips From YL Computing
- Visit the Manufacturer's Official Website to Find the Most Recent Drivers Compatible with Your System, E.g., Dell or HP. Download All Essential Drivers Related to USB Ports and Chipset Firmware Updates if Available
- Title: Comprehensive Guide on Macro Virus Infections & Effective Eradication Techniques
- Author: Kevin
- Created at : 2025-02-25 16:54:14
- Updated at : 2025-03-03 18:52:29
- Link: https://win-cheats.techidaily.com/comprehensive-guide-on-macro-virus-infections-and-effective-eradication-techniques/
- License: This work is licensed under CC BY-NC-SA 4.0.